Intel's New Vulnerability: Unraveling the Side-Channel Attack Threat
Insights | 05-05-2023 | By Robin Mitchell
Recently, new side-channel attacks have been identified in multiple Intel processors where data can be leaked through the EFLAGS register. What is a side-channel attack, how does the vulnerability work, and what challenges does this pose to engineers?
What are side-channel attacks?
The basic idea behind side-channel attacks is that although a system’s design may be secure and robust, its implementation can still be vulnerable to attacks that exploit side-channel information, such as power consumption, electromagnetic radiation, or timing variations. These attacks can reveal sensitive information such as cryptographic keys, passwords, or other confidential data the system processes.
One common type of side-channel attack on processors is known as power analysis. Power analysis attacks work by measuring the power consumption of a processor while it is executing a particular instruction or algorithm. By analysing the power consumption patterns, an attacker can infer information about the processor’s internal state, such as the values of its registers or memory locations.
Another type of side-channel attack is electromagnetic analysis, which exploits the electromagnetic radiation emitted by a processor as it performs computations. This radiation can be captured and analysed to reveal information about the processor’s internal state, including its cryptographic keys.
Timing analysis is another type of side-channel attack that exploits variations in the time it takes for a processor to perform certain operations. By measuring these variations, an attacker can infer information about the processor’s internal state, including registers or memory locations.
Real-world examples of side-channel attacks
A notable real-world example of side-channel attacks is the Spectre and Meltdown vulnerabilities discovered in 2018. These vulnerabilities affected a wide range of processors, including those from Intel, AMD, and ARM. Spectre exploited speculative execution, a feature designed to improve processor performance, to gain unauthorised access to sensitive information. Meltdown, on the other hand, targeted a flaw in the memory isolation mechanism, allowing attackers to read data from other programs and even the operating system. The disclosure of these vulnerabilities led to a massive effort by hardware and software vendors to develop and deploy patches, highlighting the potential impact of side-channel attacks on the security of computer systems and the data they process.
Another real-life example of a side-channel attack is the Rowhammer attack, which gained attention in 2014. Rowhammer targets dynamic random-access memory (DRAM) by repeatedly accessing specific memory rows, causing electrical interference that can lead to data corruption or privilege escalation. This attack demonstrated that hardware components like DRAM could also be vulnerable to side-channel attacks, further underscoring the importance of addressing these security challenges.
Protecting again side channel attacks
To protect against side-channel attacks, processor designers can employ a variety of countermeasures, such as masking, randomisation, and noise injection. Masking involves adding random values to data as it is processed to prevent attackers from inferring information from power or electromagnetic emissions. Randomisation involves adding random delays to operations to prevent timing analysis attacks. Noise injection involves adding random noise to signals, making it harder for attackers to distinguish between signal and noise.
Hardware-based countermeasures, such as secure co-processors or physically unclonable functions (PUFs), can also be implemented to help protect against side-channel attacks. Secure co-processors are separate chips designed to handle sensitive operations securely, isolating them from the main processor and making it more difficult for attackers to exploit side-channel vulnerabilities. Physically unclonable functions (PUFs) are unique, unpredictable features of a hardware device that can be used for authentication or secure key generation, further mitigating the risk of side-channel attacks. While these hardware-based solutions can offer improved security, they may come with additional costs or implementation challenges.
In addition to these countermeasures, software developers can also help protect against side-channel attacks by using algorithms and cryptographic libraries that are designed to be resistant to these attacks. For example, some encryption algorithms use “constant-time” implementations that ensure that the execution time is the same regardless of the input data, making timing attacks more difficult.
How does the new vulnerability work?
Recently, researchers from Tsinghua University, the University of Maryland, and a computer lab (BUPT) run by the Chinese Ministry of Education published their findings on a new side-channel attack that affects a number of different Intel processors. In their research paper, the authors highlight the novelty and potential impact of their work, stating, 'our work is the first that build[s] [a] side-channel [attack] with the EFLAGS register. [We] hope our work can help to improve the security of future CPUs.' Their research paper presents a novel side-channel attack that leaks information through the timing of execution and demonstrates how the EFLAGS register can be exploited (citation: Yu Jin∗, Pengfei Qiu∗, Chunlu Wang†, Yihao Yang‡, Dongsheng Wang§, Gang Qu, " Timing the Transient Execution: A New Side-Channel Attack on Intel CPUs,"). The researchers highlight that this attack does not rely on the cache system, making it difficult to be detected by existing tools or methods. As the first to build a side-channel attack with the EFLAGS register, they hope their work can contribute to improving the security of future CPUs.
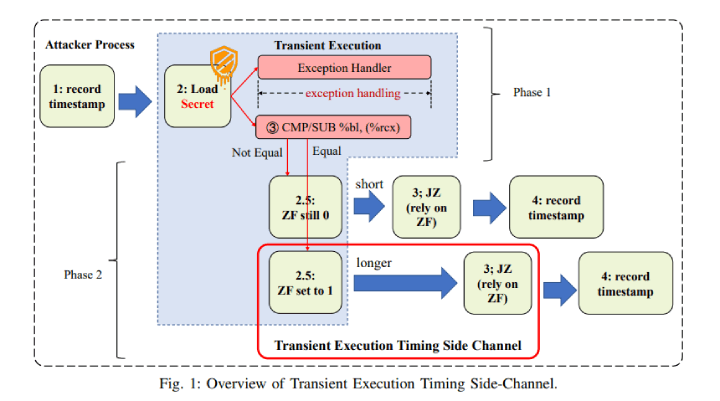
In order for this attack to work, the engineers utilised the EFLAG register, which holds the status of various conditions, such as Zero, Non-Zero, and parity. A value is placed into a register, and a small JCC routine is used (Jump if compare), which compared two values. If the second number being compared is in a protected area of memory, such as kernel space, then the result will not be delivered, and an exception thrown.
However, during speculative execution, the processor executes the instruction even if the memory being accessed is in a protected space and will proceed with the result. While the processor will deny the result to the application executing the illegal instruction, it turns out that a special combination of instructions that compare and set the zero flag if the two values being compared are equal. Thus, even though the comparison isn’t allowed to be done, there is a noticeable timing difference when the two values being compared are equal (as the zero flag needs to be set, consuming additional clock cycles).
Thus, a piece of code can perform an iterative loop, timing how long it takes to execute each instruction and determine the value of the data held in protected memory. Of course, this has to be done thousands of times, but considering the massive speeds offered by modern processors, this attack has been demonstrated to have a 100% success rate at accessing protected areas of memory.
What challenges does this pose to engineers?
According to the researchers, there is little that can be done to prevent this attack as the internal nature of the speculation system used by Intel is somewhat hidden from the public. As such, it would be up to Intel to analyse the attack and implement mechanisms into the silicon to prevent this attack from working in new CPUs. With regards to existing CPUs, the only protection methods that can help against this are heavily reliant on software implementations, and these are not trivial to deploy.
Overall, what the researchers have demonstrated here is how side-channel attacks will continue to rise in popularity as they bypass both software and hardware security systems. It might be required that future processors integrate mechanisms that ensure equal execution time for all instructions, or better, clock noise that randomises the execution time of each instruction, thereby eliminating timing attacks.

