Cryptographic Keys Theft: Hackers Can Exploit Power LEDs via Video from 60 Feet
Insights | 22-06-2023 | By Robin Mitchell
As the nature of cyberattacks continues to increase in complexity, engineers are facing increasing pressure to develop new methods to protect devices. Recently, researchers demonstrated a side-channel attack against a power LED of a smart card reader from 60 feet away and were able to recover encryption keys. What challenges do side-channel attacks present, what did the researchers demonstrate, and do side-channel attacks present a serious threat to modern electronics?
What challenges do side-channel attacks present?
In today’s digital age, the security of electronic devices and systems has become paramount. With the increasing reliance on technology in various domains such as finance, healthcare, and communications, protecting sensitive information from unauthorised access is crucial. However, modern electronics face a significant challenge in the form of side-channel attacks.
Side-channel attacks take advantage of the physical characteristics of electronic devices, such as power consumption, electromagnetic radiation, and timing information. By analysing these side channels, attackers can infer valuable information about cryptographic keys, passwords, or other confidential data. Unlike traditional attacks that target vulnerabilities in software or algorithms, side-channel attacks target the inherent physical properties of the hardware itself.
Recent research has further expanded our understanding of side-channel attacks. A team of researchers from the Ben-Gurion University of the Negev has developed a method known as 'video-based cryptanalysis', which involves recovering secret keys from a device by analysing video footage of the device's power LED. This innovative approach leverages the correlation between the device's power consumption and the brightness of its power LED, allowing attackers to infer secret keys from the RGB values associated with the LED's brightness changes during cryptographic operations12.
Challenge 1: Attack Vectors
One growing challenge presented with side-channel attacks is the increasing number of attack vectors. Modern electronic devices generate a multitude of side-channel leakages, including power consumption variations, electromagnetic emanations, and acoustic emissions. Addressing all these potential leakage sources poses a significant challenge, as each requires tailored countermeasures.
Challenge 2: Detection
Side-channel attacks are often subtle and difficult to detect and, in some cases, impossible. Traditional security measures, such as encryption algorithms, are ineffective against such attacks as side-channel attacks typically bypass security measures entirely. Detecting and quantifying side-channel leakages require specialised equipment, advanced signal processing techniques, and expertise in cryptography and hardware design.
Challenge 3: Countermeasures
Developing effective countermeasures against side-channel attacks is a complex task, as countermeasures must balance security, performance, and cost considerations. Additionally, these countermeasures need to be implemented at different levels, including hardware, software, and system design, making the process challenging and time-consuming.
There are several types of countermeasures that can be implemented to protect against side-channel attacks:
Hardware Countermeasures
Hardware countermeasures involve designing the physical components of a system to reduce or eliminate side-channel leakages. This can include techniques such as:
- Power Analysis Resistant Chips: These chips are designed to have a constant power consumption, regardless of the operations being performed, making it difficult for an attacker to infer any useful information from power analysis.
- Shielding: Physical barriers can be used to block electromagnetic emanations, preventing attackers from capturing these signals.
- Noise Generation: By introducing random noise into the system, it becomes harder for an attacker to distinguish between the noise and the actual side-channel signals.
Software Countermeasures
Software countermeasures involve modifying the software or firmware running on a device to reduce side-channel leakages. This can include techniques such as:
- Constant-Time Programming: By ensuring that operations take a constant amount of time regardless of the input, timing attacks can be mitigated.
- Randomization: By randomizing the order in which operations are performed or the data that is processed, it becomes more difficult for an attacker to correlate side-channel signals with specific operations or data.
System-Level Countermeasures
System-level countermeasures involve designing the overall system in a way that reduces the risk of side-channel attacks. This can include techniques such as:
- Secure Key Management: By securely managing cryptographic keys (e.g., regularly rotating keys, securely storing keys), the impact of a successful side-channel attack can be minimized.
- Multi-Factor Authentication: By requiring multiple forms of authentication, an attacker who is able to recover a single factor (e.g., a password) through a side-channel attack will still not be able to gain unauthorized access.
While these countermeasures can significantly reduce the risk of side-channel attacks, it is important to note that no countermeasure is 100% effective, and a layered approach that combines multiple countermeasures is often the most effective strategy.
Challenge 4: Performance Impact
Implementing countermeasures against side-channel attacks often comes at the cost of increased power consumption, reduced processing speed, or increased hardware complexity. Balancing the performance impact of countermeasures while maintaining acceptable security levels poses a considerable challenge, especially for resource-constrained devices such as Internet of Things (IoT) devices.
Researchers demonstrate a side-channel attack against power LED from 60 feet away
To demonstrate the potential dangers posed by side-channel attacks, cybersecurity researchers recently published their findings on a newly developed attack that is capable of recovering secret encryption keys used in a smart card reader. The attack took advantage of the fact that during operation, the power LED flickers, and by understanding the inner workings of the card reader, it is possible to decode the keys used to allow access.

The researchers demonstrated the application of video-based cryptanalysis by performing two side-channel cryptanalytic timing attacks. They were able to recover a 256-bit ECDSA key from a smart card by analysing video footage of the power LED of a smart card reader via a hijacked Internet-connected security camera located 16 meters away from the smart card reader23.
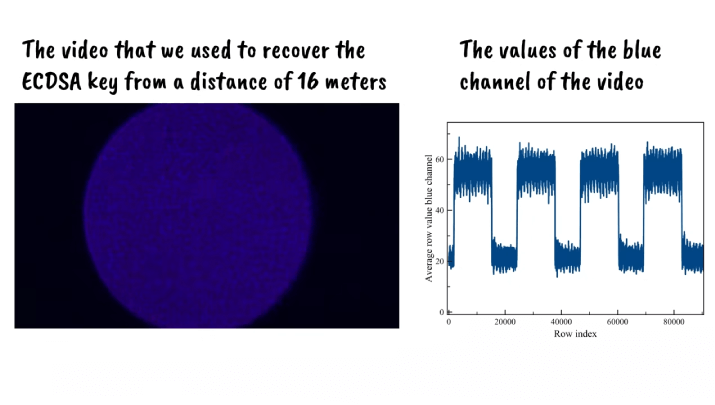
They also managed to recover a 378-bit SIKE key from a Samsung Galaxy S8 by analysing video footage of the power LED of Logitech Z120 USB speakers that were connected to the same USB hub used to charge the Galaxy S823.
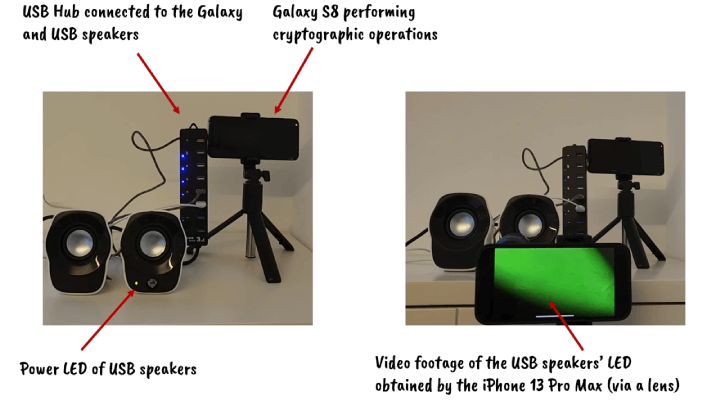
But simply observing an LED with a camera is not enough to recover such data, even with high-frame rates. In order to make standard off-the-shelf cameras found in webcams and smartphones successfully record rapid changes in an LED’s brightness, the researchers turned to the rolling shutter effect, where camera sensors record images line by line instead of the entire image sensor.
As such, each line of a camera’s sensor represents an extremely small time frame. For example, a frame rate of 60fps with a vertical resolution of 1080 lines would make each line equivalent to 0.16ms / 1080 = 15us. Doubling the frame rate and resolution (4K @120fps) would further decrease this to 3.75us. If an LED is zoomed in on and reduced in focus (to cover a larger area on the sensor), it is very easy to record individual changes in LED brightness during different processing operations, including decoding bits from a secret key.
“One of the most significant things of this paper is the fact that you don’t need to connect the probe, connect a scope, or use a software-defined radio. It’s not intrusive, and you can use common or popular devices such as a smartphone in order to apply the attack. For the case of the Internet-connected video camera, you don’t even need to approach the physical scene in order to apply the attack, which is something you cannot do with a software-defined radio or with connecting probes or things like this.” - Ben Nassi, lead researcher of the attack.
This sentiment is echoed by Dan Goodin, a technology journalist at Ars Technica, who noted that the new method of attack 'removes the biggest barrier holding back previously existing methods from exploiting side channels: the need to have instruments such as an oscilloscope, electric probes, or other objects touching or being in proximity to the device being attacked'4.
Do side-channel attacks present a serious threat to modern electronics?
Luckily, side-channel attacks are currently an exception and not the norm primarily due to their complex nature. It is highly unlikely for cybercriminals to start monitoring the power consumption of a device or the brightness of an LED, but that isn’t to say that it won’t happen in the future. As technology continues to improve, so will the tools used by cybercriminals, and side-channel attacks could become a popular method of attack.
For instance, the recent 'Hertzbleed' side-channel attack demonstrated how power analysis could be used to leak secrets from a device. In this case, the attacker was able to measure the power consumption of a device while it was performing cryptographic operations and use this information to infer the secret key5.
Indeed, the researchers behind the video-based cryptanalysis method believe that the future of such attacks could be significant, especially considering the expected improvements in video cameras’ specifications2.
For the time being, it is important that engineers utilise strong security measures to defend against widely used attacks such as code injection, buffer overflows, and weak passwords. However, it might be worthwhile for engineers involved with security hardware design to start considering methods for balancing power consumption so that energy-intensive operations have a consistent power profile.
As the researchers suggest, using the most updated cryptographic libraries available can be an effective countermeasure against such attacks2.
For example, cryptographic libraries such as OpenSSL have implemented countermeasures against side-channel attacks, including constant-time cryptography, which ensures that the time taken to perform cryptographic operations does not depend on the secret keys. Additionally, hardware countermeasures such as power analysis-resistant chips can also be used to protect against these types of attacks5.
References:

