33 Critical Vulnerabilities Found in Popular IoT Protocol MQTT
IoT | 09-02-2022 | By Robin Mitchell
Researchers conducted a study on the popular MQTT protocol and found 33 vulnerabilities, highlighting the need for stronger cybersecurity measures in IoT and IIoT devices that use this messaging protocol. The vulnerabilities could lead to cyberattacks that compromise the security of sensitive data being transmitted via MQTT, which operates on a message queue transport system, allowing devices to subscribe to and publish messages on various topics. The vulnerabilities affect MQTT implementation worldwide, and while encryption can be deployed in MQTT, it is not a requirement, leaving devices open to attack. What is MQTT, how have vulnerabilities plagued MQTT, and what will engineers need to consider moving on?
What is MQTT?
Message Queue Telemetry Transport, or MQTT for short, is a widely used messaging protocol found mainly in the IoT industry. MQTT itself is not concerned with the hardware that it runs on, nor does it care about how messages are sent (for example, MQTT can be sent down UART, Ethernet, RS-232, and CAN); it operates in the application layer. Other examples of protocols that operate in the application layer include HTTP, FTP, TLS/SSL, and SSH.
The core principle of MQTT is that devices can talk to servers (called a broker) and receive data from servers, but while protocols such as HTTP have a very specific client/server response, MQTT messages on either side can happen at any moment. Let’s look at a basic setup to better understand how this works.
Several IoT devices (clients) are connected to a central server (broker), and these IoT devices all subscribe to a variable called “temperature”. Whenever that variable changes value, all devices subscribed to that variable will receive a message from the server that it has changed and its latest value. Thus, if any one of those devices sends a message to the server to change the value of “temperature” (called publish), then all other devices on the network will receive the latest value of “temperature”.
Devices in MQTT are always connected to the server, and the small size of MQTT messages makes it ideal for use in IoT applications. Furthermore, the ability to receive messages from a connected server at any time allows for remote devices to be controlled without needing to wait for an update event on the client side.
To summarise:
- A central server is called a broker
- Clients are always connected
- Client subscribe to variables (called topics)
- Changing the value of a topic is called “publishing”
- The moment a topic is changed in value, all clients subscribed to that topic will receive an update
- Both the broker and client can initiate a message
Researchers identify 33 vulnerabilities in MQTT
Recently, Kaspersky security experts turned their eyes to MQTT to see how many vulnerabilities remain in the largely popular IoT protocol, and the result was 33, with 18 of those being critical. This is an increase from 23 vulnerabilities found in 2020. Considering that a large percentage of IoT devices use MQTT, many millions of devices worldwide are potentially vulnerable to attacks on MQTT. According to Kaspersky research, 91% of healthcare providers worldwide have adopted telehealth, but this has led to new security risks, particularly with patient data.
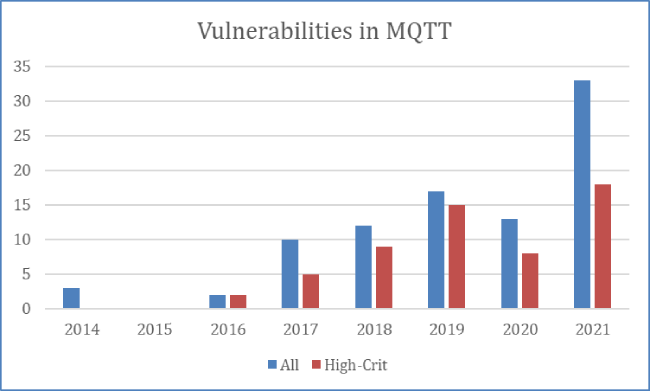
From 2014 to 2021, there were several vulnerabilities discovered in the MQTT protocol.
The researchers noted one interesting fact that while encryption can be deployed in MQTT, it is not a requirement, meaning that connection requests, device login, and message transfers can be done entirely unencrypted. While data such as temperature and humidity may be benign, other devices could transmit more personal details (such as bio signs from wearable medical devices). This means that attackers would be able to see data that could be used to identify what tasks individuals are doing. Furthermore, it potentially allows attackers to perform man-in-the-middle attacks and send false data.
The same researchers also looked at other platforms and protocols, and one that stood out in their findings was the Qualcomm Snapdragon Wearable Platform which is specifically used for creating medical wearable devices. According to the researchers, they identified over 400 vulnerabilities in the device despite being launched several years ago.
What will engineers need to consider moving forward?
MQTT is a great protocol for reducing energy requirements, simplifying connectivity, and providing servers with the ability to message connected clients directly. However, engineers must understand the fundamentals of the protocol and research if their implementation follows standard safety protocols.
For example, MQTT libraries that do not use encryption by default should be dropped, and the use of strong passwords and API keys is a must. Because MQTT is nothing more than a protocol, it can be easily used on top of encrypted messaging systems such as TLS/SSL. This would instantly force devices to store server certificates while allowing individual clients to access certificates. Thus, only connections where both parties (server and client) have authentic certificates can be processed, and man-in-the-middle attacks are impossible.
Other protocols exist, and there is no real need for every IoT device to use the same protocol if such a device has no intention of working on other systems. However, as we move forward, we must consider the security impacts of what we create and challenge anything that is a standard. Simply put, never assume that an existing library is secure and never trust that a system will work without studying it at a source code level.

