Ambient Light Sensors & Surveillance: What You Need to Know
Insights | 09-02-2024 | By Robin Mitchell

MIT Computer Science and Artificial Intelligence Laboratory researchers indicate that smartphone ambient light sensors could be exploited by hackers to surveil users.
Key Things to Know:
-
Ambient Light Sensors as Potential Surveillance Tools: Recent MIT research reveals that ambient light sensors, commonly found in smart devices, could be exploited to function like cameras, capturing images without users' knowledge.
-
Privacy Legislation and Sensor Security: Despite new laws in the UK, EU, and US demanding higher security standards for IoT devices, many products still fail to protect privacy adequately, underscoring the need for stringent sensor access permissions.
-
The Misconception of Harmless Sensors: Engineers often overlook the potential privacy threats posed by basic sensors, leading to lax security practices where devices can access sensors without user permission.
- Urgent Need for Enhanced Security Measures: The findings stress the importance of developing new strategies, both in hardware and software, to mitigate privacy risks. This includes reevaluating sensor access permissions and implementing robust security protocols to ensure user privacy.
Introduction
Ambient light sensors are commonplace among electronic devices, and while they have always been seen as benign, new research has demonstrated how they could potentially be used as cameras. What challenges do basic sensors introduce for privacy, what did the researchers demonstrate, and what does this mean for sensors in devices going forward?
What challenges do basic sensors introduce in privacy?
Ensuring privacy in electronic devices has become one of the single most important factors in any modern design. Not only do consumers expect their devices to not monitor their calls or unexpectedly activate cameras, but even governments around the world are introducing rules to prevent potentially dangerous products from entering the market.
For example, the UK, EU, and US have all introduced legislation that requires IoT devices to have a basic level of security, including unique passwords by default, requiring clear permission from users when accessing sensors, and ensuring that manufacturers provide updates when vulnerabilities are discovered. But even though strong privacy measures are finally making their way into products, there are still numerous devices on the market that fail to meet these needs.
Making matters worse, there is still a tendency amongst engineers to ignore the potential dangers that sensors can introduce. Just as when the first IoT devices came onto the market, it is generally believed that sensors such as thermistors, photodetectors, and humidity sensors are all benign and pose no threat to privacy.
However, the truth is that even the most basic sensor can pose a threat, whether that involves giving backdoor access to a system or allowing the device to monitor its surroundings. Thankfully, making these sensors violate an individual's privacy is no small feat, but the blanket assumption that they can't be used for nefarious reasons is leading to poor security practices, such as the ability for devices to access sensors without asking for permission.
Researchers demonstrate ambient light sensor-based camera
Recent studies, such as the one conducted by MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL), have unveiled that ambient light sensors in smart devices could potentially be exploited to capture images without a camera. This innovative research demonstrates that by manipulating the light intensity captured by these sensors, it's possible to reconstruct images of the environment in front of the screen, revealing a new dimension of privacy risks associated with common device components. This finding underscores the need for a reevaluation of sensor access permissions and the implementation of more robust security measures to safeguard user privacy.
To demonstrate the challenges that even the simplest sensors can introduce for privacy, a team of researchers from MIT recently demonstrated how ambient light sensors in TVs and tablets can be turned into a camera, with the ability to track hand gestures across the screen.
The method that the researchers developed closely resembles light guns used in old retro game consoles, whereby pressing the trigger on the light gun results in a momentary blank screen with a small rectangle shown over the target. If the light gun's light sensor can see the square, then the game knows that the gun was pointed at the target; otherwise, the target was missed.
Bridging Classic Concepts with Modern Privacy Concerns
The study published in Science Advances by Yang Liu and colleagues from MIT further elaborates on the technical feasibility of this privacy threat. The researchers demonstrated that even without direct access to a camera, the ambient light sensor, when combined with a specific display content, can capture detailed images of user interactions. This technique, while currently limited by resolution and speed, opens up discussions on the necessity of developing new hardware and software strategies to mitigate such privacy risks. It emphasises the importance of incorporating privacy considerations into the early stages of device design, moving beyond traditional security measures to address these emerging threats.
Fig. 1. Imaging setup with primal and dual configurations.
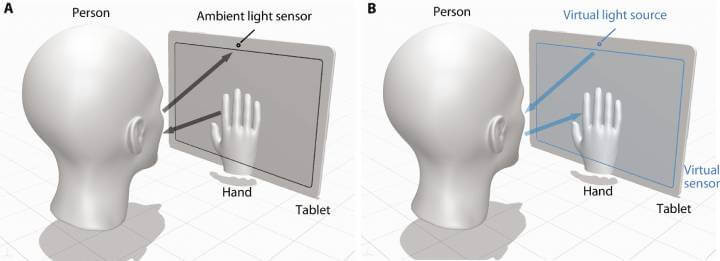
- (A) Primal configuration: where the screen displays a sequence of patterns and the ambient light sensor receives the light first partially blocked by the interacting hand and then reflected from the human face.
- (B) Dual configuration: where the ambient light sensor works as the virtual point light source and the pixelated screen as the virtual sensor. No lens is required between the screen and the scene to form an image on the virtual sensor, because the interacting hands create in-contact shadows on the virtual sensor, forming one-to-one mapping between the target scene pixel and the sensor pixel.
In the case of the researchers, if a screen containing an ambient sensor can be made to show a specific video pattern, it is possible to read the data back from the ambient sensor and reproduce images. This video pattern didn't necessarily require the entire screen to function, meaning that it is possible for a video to be embedded on a website or other app that briefly plays as the user scrolls past it.
To make matters worse, the ambient light sensor (which is generally used to control the brightness of the screen) doesn't require any user permission and is always on. This means that it is possible for the device to constantly monitor device usage. Furthermore, with the ability to determine gestures and the area of the screen being used, it is possible to recover pin numbers and patterns used to unlock the device.
In light of these findings, the development of countermeasures to protect against such vulnerabilities is crucial. Recommendations from the research suggest limiting the precision and speed of ambient light sensors through software updates and considering their placement in device design to reduce the risk of unauthorised data capture. These measures, along with increased transparency and user control over sensor access, could play a pivotal role in enhancing device security and user trust, aligning with the principles of Google's E-A-T criteria.
What does this mean for sensors going forward?
While such an attack is unlikely to be used by hackers due to the extreme difficulty involved in recovering data from the ambient light sensor and playing a specific video file, it does demonstrate that attacks against sensors are more than possible. As such, engineers should always treat any sensing-capable component as a potential weak point and put in measures to prevent its misuse.
For example, ambient light sensors on phones, tablets, and TVs should have a refresh rate limitation in hardware that prevents rapid access to the sensor (this could be achieved with a sample and hold circuit and oscillator). In the case of humidity and temperature sensors, these should also have hardware limitations to prevent rapid sensing as well as restrict what processes can access those sensors.
Overall, what the researchers demonstrated shows how even the most basic sensor can be used to invade privacy, and considering how attacks are becoming ever more complex, it won't be long before attacks against these common sensors become commonplace.

