Intel to Introduce Control-Flow Enforcement Technology into Tiger Lake Mobile CPUs
| 09-07-2020 | By Robin Mitchell
Intel have announced that a new anti-malware system will be introduced into its Tiger Lake mobile CPUs. What does this new security technology do, and how is hardware security playing an ever more important role in everyday electronics?
Hardware Attacks and Security
For the longest time, the vast majority of security measures came from software implementations that would look for malicious programs running on a computer, monitor network activity to stop suspicious connections, and create backups so that in the event of an attack information can be restored. The reason for this is that almost all attacks on computing systems were remote, and thus only the software layer of a machine was accessible. If, however, a computer or device can be physically accessed then an attacker can perform a whole range of physical attacks ranging from data theft to outright control.
Software such as anti-virus works well when dealing with software attacks as both operate in the same domain. For instance, it is easy for an operating system to monitor what an application is doing, and then halt the process if it accesses areas of memory where it shouldn’t, or attempts to overwrite files outside of its immediate directory. However, how can software prevent an attack in hardware? How does anti-malware software prevent an attacked from physically probing data lines or exploiting the processor in special scenarios such as restarts? The answer is that it is very difficult, and once an attacker has access to the physical hardware there is very little that an OS can do.
Before mobile devices, almost all technology that incorporated a processor was relatively safe from hardware attacks as they would often be confined to a room or office. Now that we live in a very mobile world, with smartphones being unavoidable, and the estimated +30 billion IoT devices globally means that hardware attacks are now a real threat. As a result, security hardware is increasingly becoming popular with many SoCs integrating cryptographic accelerators, true random number generators, secure boot methods, and on-the-fly memory encryption. Continuing this trend is Intel with its announcement on the inclusion of Control-Flow Enforcement technology into its latest Tiger Lake Mobile CPUs.
Control-Flow Enforcement
Since 2016, Intel have been developing their Control-Flow Enforcement technology includes a set of silicon-level (i.e. machine code), instructions that protect against control-flow hijacking. Control-flow attacks are those which exploit common bugs found in programs including buffer overflows, stack exploits, and integer overflow attacks. For example, if an attacker can get access to a program’s stack then, in theory, the attacker can get the program to jump to arbitrary locations (such as the location of a hacker’s code). It is difficult for an operating system to detect these attacks especially those that run on low-end hardware such as smartphones.
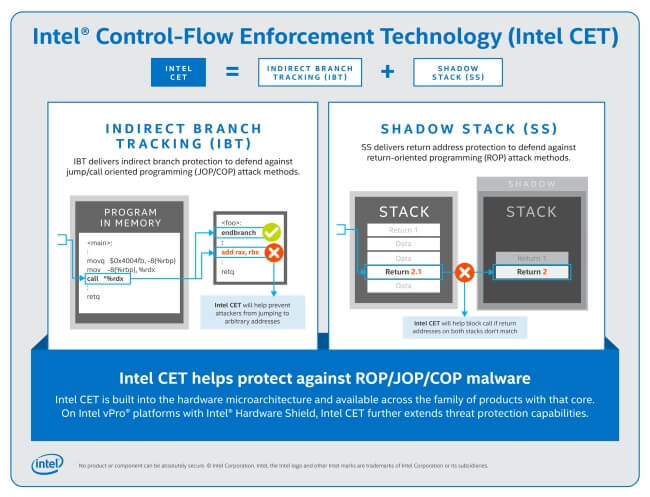
Credit: Intel Newsroom
To help combat these attacks, Intel are integrating their Control-Flow Enforcement technology into their Tiger Lake Mobile CPUs. The first feature that CET integrates is the shadow stack which provides return address protection. This means that when a piece of code makes a call to a routine, the address is not only pushed onto its normal software stack, but to a special shadow stack that cannot be accessed by an attacker. If the address on the shadow stack and the normal stack do not match then the processor will block the return. The second protection method provided by CET is the use of indirect branch tracking (IBT). While not entirely explained in operation, the IBT protects applications in scenarios where CPU jump tables are used. IBT is designed to protect against Jump Oriented Programming and Call Oriented Programming.
“Intel was the first to tackle these complex security challenges and we remain committed to working with the industry to drive security innovation. We recognized that scaling OS and application adoption to truly solve the problem would require industry-wide collaboration. To accelerate adoption, we published the Intel CET specifications in 2016.”
-
Tom Garrison, vice president and general manager of client security strategy and initiatives at Intel

