Will SOTA updates help hackers steal your car?
| 09-02-2022 | By Paul Whytock
The answer to that is yes, depending on the level of SOTA capability your car has and its level of communication security. But what is SOTA?
Fundamentally, Software Over The Air is a way of updating the software-controlled functions of a car by sending updates via a WiFi or mobile network. These would come from a cloud-based server direct to the vehicle or to the owner’s device and then be uploaded to the vehicle.
In principle, it’s no different to the software updates we get to our smartphones and laptops, although let’s hope that they are not as annoying as some of those that are foisted upon us. There would, in fairness, be one significant major difference. That is, vehicle software updates would have to be guaranteed as safe and that such downloaded vehicle software updates in no way made operating the vehicle dangerous.
They would also have to be hacker-proof. There are already documented incidences of malicious hackers taking over control of a vehicle with dangerous intent.
Relative to the safety aspect is that SOTA update files would be transmitted as delta versions rather than a full software installation file. In effect, the vehicle manufacturer would only send a partial software update that only affects the vehicle component or system that requires modification.
But SOTA vehicle downloads must be secure, and the major challenge here for the carmakers is how to ensure only protected and authorised updates that are issued by them are accepted and downloaded by the vehicle in question.
This is imperative because updates transmitted by SOTA can impact the software that controls the vehicle’s physical components, electronic processing systems, infotainment, and critical safety systems.
Fixing The Problems
Being able to update cars via SOTA is, of course, very attractive to the carmakers and the majority of customers. There is a far faster and more convenient way to have software related or software-controlled problems fixed or to make modifications and improvements rather than obliging owners to go through the rigmarole of making an appointment to visit a dealer and wait while the software fix is implemented. It is better to get that all done by downloading the software update while your car is parked at home.

It’s a win-win solution, although this view is not shared by many car dealerships as they see it as a revenue loser.
According to a survey conducted by technology consultants Bearing Point, SOTA simplifies the vehicle configuration and purchase decision process for customers as vehicle features and accessory systems can be easily added at a later stage of ownership if required.
Drivers of electric vehicles can benefit from over-the-air updates. SOTA can unlock limited battery capacity and increase vehicle performance and range. Some customers will be willing to pay for value-added SOTA updates and new features. This latter point is a smart money-maker for the carmakers as the level of SOTA updates could become a proposition that customers are willing to pay for just as they pay for additional accessories that are not part of the standard build of a vehicle.
Security Concerns
All that sounds positive but constantly lurking in the background is the security risks that SOTA may facilitate.
Because of the flexible data connectivity of a vehicle to another vehicle or an infrastructure, new risks may occur during the data transmission. As risk can be defined as a likelihood of an attack caused by a threat, risks of unauthorised access to a vehicle’s software via the interconnectivity has to be rapidly identified and resolved by providing additional safeguards in the data transmissions.
The possible attacks to a SOTA system might include identity theft and manipulation or repetition of transmitted messages, resulting in hackers gaining control of the vehicle. This encompasses intellectual property theft of software images or sensitive vehicle data. An attacker possessing the OEM server’s identity could infiltrate the electronic system and install fraudulent software on the ECUs (electronic control unit) of many thousands of vehicles.
However, Bearing Point also thinks that software issues and bugs could severely impact passenger safety and vehicle performance and lead to many recalls. Over 8 million vehicles were recalled in the past few years involving some of Germany’s top brands, and nearly 4 million of those were related to software problems.
In general, carmakers like the look of SOTA with Porsche, Ford, Volvo, BMW, Toyota and Tesla already embracing the technology. German auto technology company Robert Bosch say that some of today’s vehicles already feature over 100 control units and that this is only going to increase. Accordingly, the company is now heading a consortium of companies and research institutions, including Mercedes-Benz, in the Software-Defined Car (SofDCar) project, which establishes rules and processes for controlling all future software updates and upgrades.
It’s true to say that plenty of work is happening to boost vehicle Internet-related security. Intel Security, for example, has looked at secure boot-up loaders that check the digital signatures of all software about to be run on each ECU, active memory protection to protect against overflow conditions that malicious code can exploit, and virtualisation using software containers in which downloaded code is run.
Intel believes there is a need to protect both the cloud end and the in-vehicle end of the link, including encrypted communications, threat intelligence exchanges and databases and credential management where everyone in the SOTA value chain is authenticated via federated identities using cryptographic keys.
The Holistic Approach
Add to all this the fact that today’s vehicle systems can be infiltrated via cellular, satellite, WiFi, Bluetooth, USB, OBD II and wireless remote keys. Intel recommends a holistic approach where it is insufficient to just firewall the SOTA cloud from the car. There must be onboard vehicle protection for those attacks where one of the non-SOTA entry points are used.
Symantec has also released a white paper on vehicle security which focuses on protecting the various layers of the connected car architecture, from the cloud-based layer, through the radio layer, to the single-board computer (SBC), body control module (BCM) and various ECUs, down to the smaller sensor modules, the chips driving those modules, and the bus protocols connecting them all together including the commonly used Controller Area Network bus (CAN bus).
The company’s work indicates it will take many years to truly secure all aspects of the connected car but that an essential starting point should be to lock down the head unit, which is often the most powerful SBC (single board computer) in the vehicle and then to use the head unit as a way of managing and updating the rest of the car.
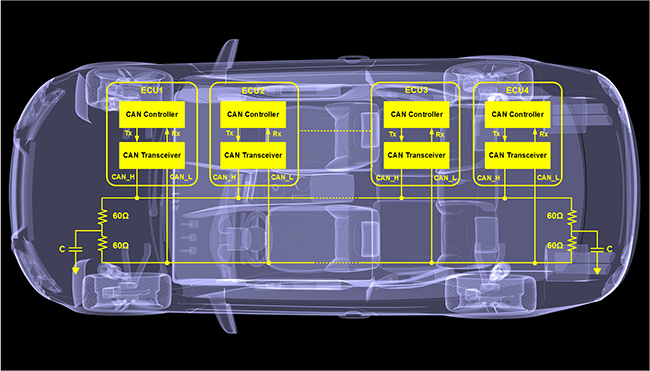
Symantec’s techniques include white-listing code that is pre-approved and controlling how that code is permitted to behave, running code in sandboxes and monitoring code and activity across the CAN bus, over the air and within the modules to detect and deal with suspicious or incorrect situations.
Secure Manufacturing
There is absolutely no doubt that ensuring SOTA is secure will be the combined responsibility of the vehicle manufacturers and their suppliers of related software and electronic components. ESCRYPT, an automotive cybersecurity solutions specialist, supports this view and is adamant that automotive security starts production at the design and production stage.
At this point, vehicles and their individual components must be protected against cyber-attacks and data theft. If, for example, hackers infect the vehicles’ ECUs with malware during production and gain access to their cryptographic material, the results would be disastrous.
The company believes its security solution for distributing and inserting certificates and cryptographic keys during ECU production would increase final vehicle security. Critical material provided by the carmakers is distributed amongst its production sites. It is stored on production key servers in readiness to be implemented into the ECUs during the manufacturing process.
This technique can be integrated into existing factory IT infrastructures to ensure that the ECUs perform IT-secured data exchange in the vehicle. Avoiding the Lawsuits
Carmakers see SOTA as a very powerful revenue earner that provides customers with a shed-load of purchase options and future add-ons for their vehicles (at a price, of course) and a very convenient way of fixing some vehicles recall issues.
This is okay, providing automotive manufacturers don’t get into a marketing race to try to be the provider of the most attractive and innovative SOTA update packages.
Such marketing pressures would inevitably increase the possibility of software security lapses and potentially land the carmakers and associated suppliers with some hugely expensive lawsuits and damaging publicity.

